Your office just got some new speakers, but you can’t get the Windows app to talk to it?
This serves as a dual guide, firstly on how to create and deploy firewall rules using Intune, and secondly how to make that Sonos speaker work!
Not Connected
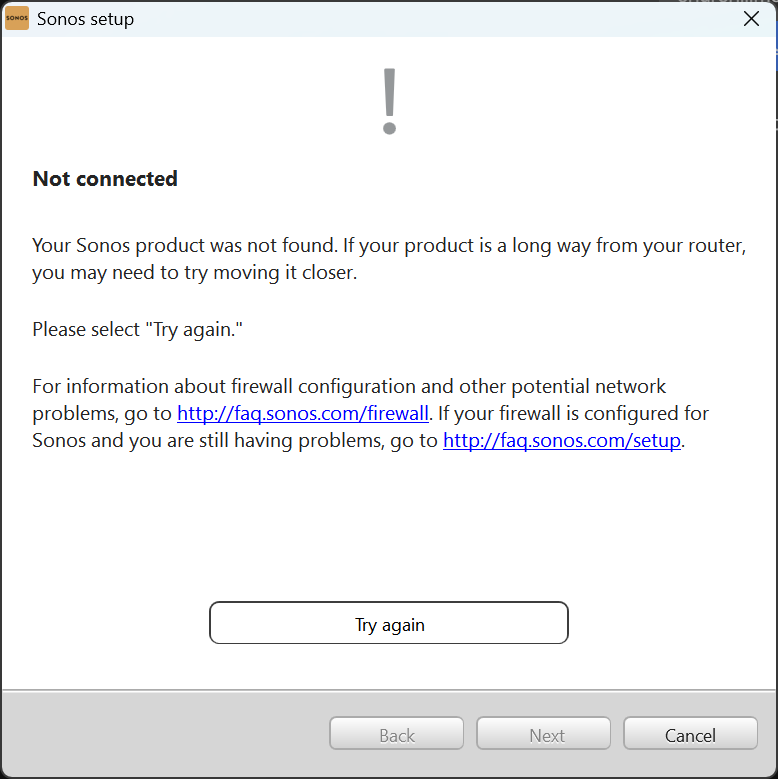
The first annoying thing you’ll see when trying to use Sonos on Windows is this message. You’ll see this if you’ve set “Allow local policy merge” to False. This means Intune is the source of truth for firewall rules and the locally created rule by the Sonos installer is ignored.
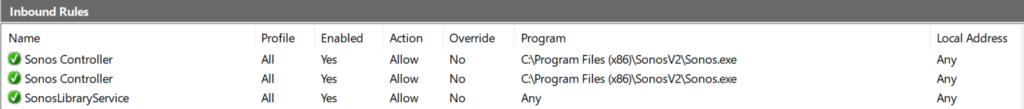
Here are those inbound rules:
Using Intune to create Firewall rules
In Endpoint Security –> Firewall –> Create a profile with type: Windows Firewall Rules
I give my general profile a name, then I begin to create the rules within the profile:
- Sonos Controller TCP
- Sonos Controller UDP
- Sonos Library Service
I worked backwards from what I could see locally set on the device, so the first two rules look identical other than the protocol numbers, 6 and 17.
| Setting Name | Value |
| Enabled | Enabled |
| Interface Types | Wireless, Lan |
| File Path | C:\Program Files (x86)\SonosV2\Sonos.exe |
| Edge Traversal | Disabled |
| Network Types | FW_PROFILE_TYPE_DOMAIN, FW_PROFILE_TYPE_PRIVATE, FW_PROFILE_TYPE_PUBLIC |
| Direction | The rule applies to inbound traffic |
| Protocol | 6 (and 17 on your other rule) |
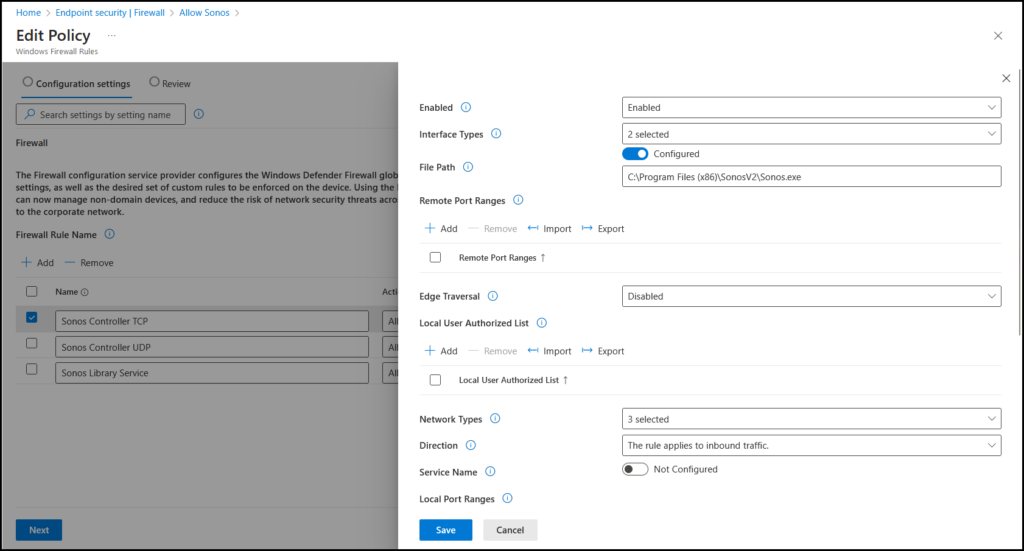
For the Sonos Library Service rule:
| Setting Name | Value |
| Enabled | Enabled |
| Interface Types | WAN, Lan |
| Network Types | FW_PROFILE_TYPE_DOMAIN, FW_PROFILE_TYPE_PRIVATE, FW_PROFILE_TYPE_PUBLIC |
| Direction | The rule applies to inbound traffic |
| Local Port Ranges | 3445 |
| Remote Address Ranges | LocalSubnet <– Enter in box like that |
| Protocol | 17 |
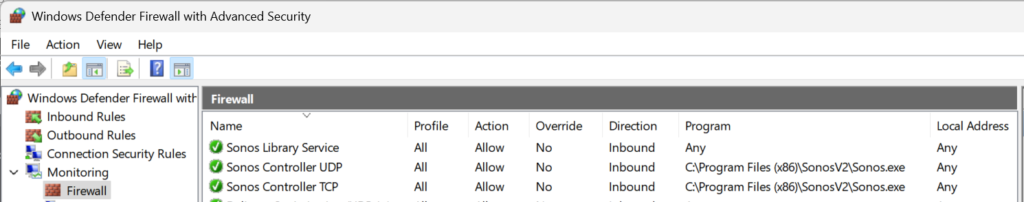
My rules ended up looking like this:
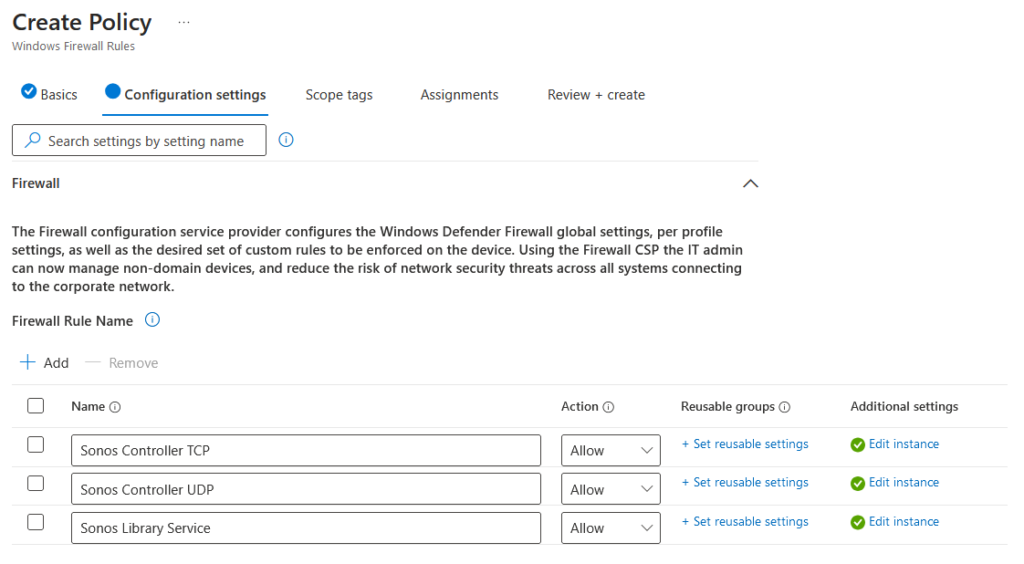
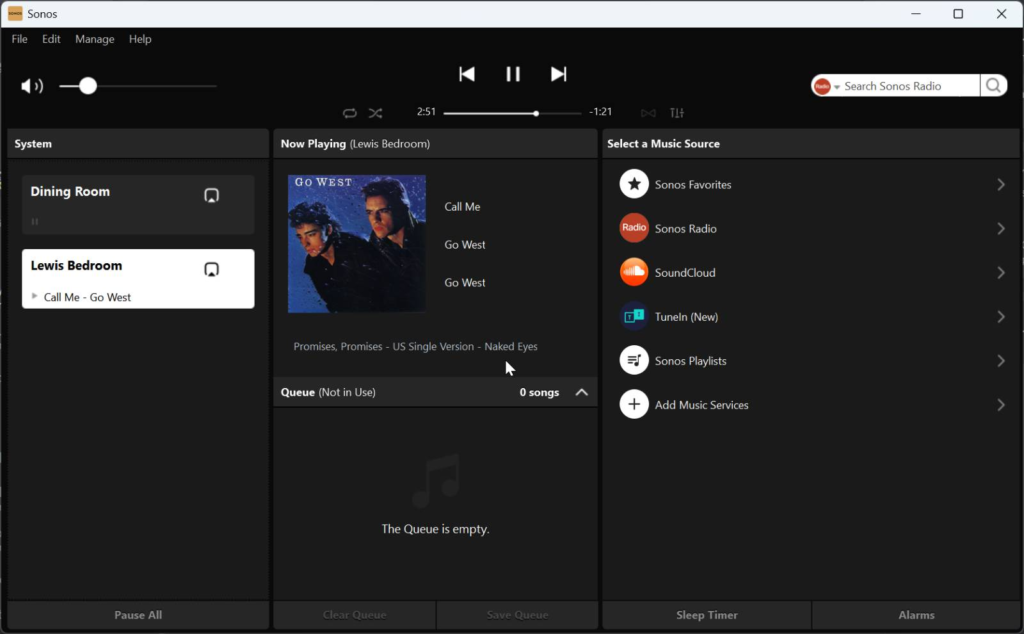
I applied it to my target devices and waited… and after rebooting:
You can check your Intune deployed rules on the device under Monitoring –> Firewall: